Palo Alto networks (PAN-OS 8.0) RADIUS integration
This guide has been documented for integration on Palo Alto PAN-OS® 8.0.
Define a RADIUS Server profile
Go to the Device tab, then choose Server Profiles > RADIUS
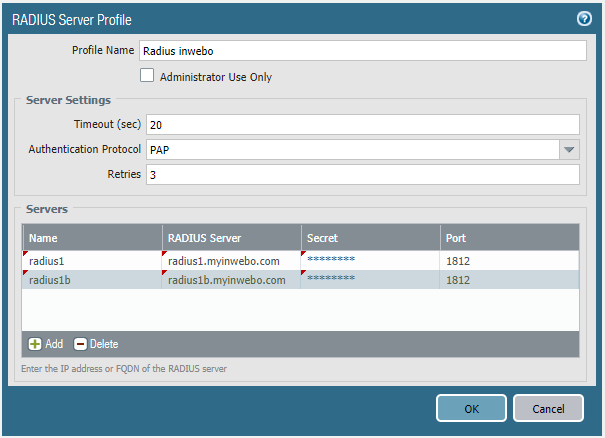
Click Add and declare the inWebo RADIUS pair you want to use. Make sure the "Timeout" and "Retries" values suits you needs. You can check our guide Redundancy and RADIUS-client configuration for best practice.
The Authentication Protocol must be set to PAP
Configure an Authentication profile
Within the Device tab click on the Authentication Profile menu
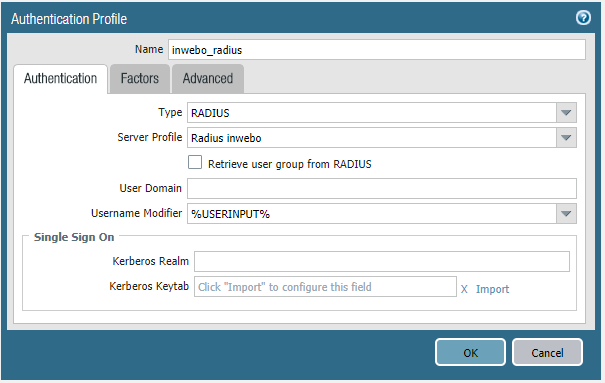
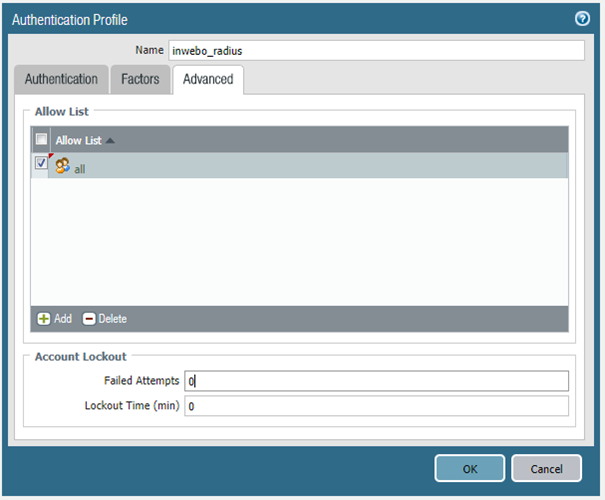
Click "Add", change the type to "RADIUS" then choose the Server Profile previously configured. Leave the "Factors" tab default configuration. In the "Advanced" tab make sure you allow your users to use this Authentication profile.
Use inWebo to authenticate your users
Notice : if your policies uses LDAP user groups you'll need to keep an LDAP authentication to retrieve the user group membership. inWebo doesn't know which LDAP user group your users are member of.
The user will connect using an OTP generated by an inWebo token or by receiving a push notification on his mobile.
You may want to use MFA to control access to the GP Portal and/or the GP Gateway. If you choose to setup inWebo MFA for both Portal and Gateway then users will have to do MFA for both.
Typical setup enforce a login and password authentication on the GP Portal and inWebo MFA authentication on the GP Gateway.
Configure the Global Protect Portal to use TrustBuilder MFA
Go on the Network tab and choose Global Protect > Portals menu
Add a Global Protect Portal configuration or edit an existing GlobalProtect Portal configuration
In the Authentication tab, declare a Client Authentication and choose the Authentication Profile you created
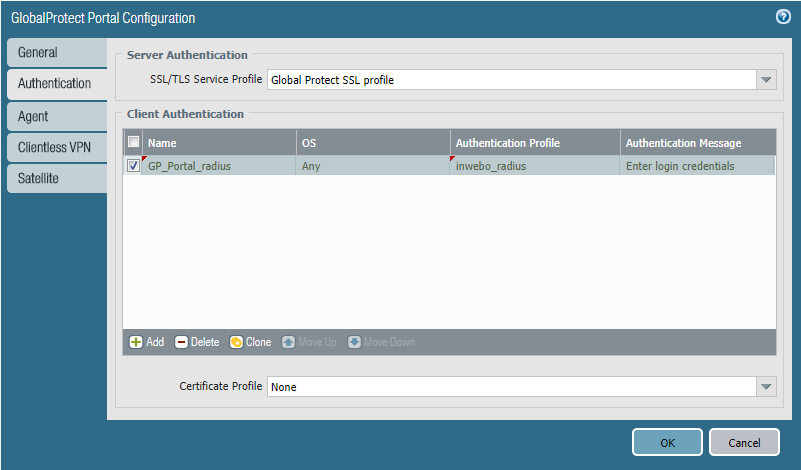
Configure the Global Protect Gateway to use inWebo MFA
The GP Gateway authenticates the user after the GP Agent succesfully authenticated the user against the GP Portal.
Go on the Network tab and choose Global Protect > Gateways menu
Add a Global Protect Gateway configuration or edit an existing GlobalProtect Gateway configuration
In the Authentication tab, declare a Client Authentication and choose the Authentication Profile you created
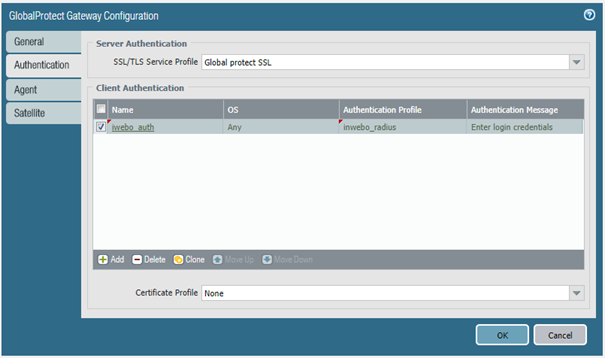
Configure inWebo
You can create your own InWebo account at InWebo Signup page. This will give you access to your InWebo Administration Console.
- Once connected, go to Secure Sites tab > CONNECTORS section.
- Select “Add a connector of type…”, and choose “RADIUS” or “RADIUS Push” :
- The popup below will appear. Enter the public IP addresses used by your Palo Alto Gateway, along with the RADIUS secret you have defined earlier. Double check the IP addresses as the Palo Alto Gateway can be configured to use a specific interface/IP to authenticate the users.

