inWebo LDAP Proxy v1.6 installation and configuration
Release notes
LDAP Proxy 1.6.1 (January, 2022)
New parameter ldap.proxy.max.simultaneous.push for managing parallelization (more details)
LDAP Proxy 1.6.0 (September, 2021)
Optimization of the send notification mechanism
Adding an optional Heartbeat to detect network failures
New parameters to optimize HTTPS API communications
Adding TLS 1.2
Introduction
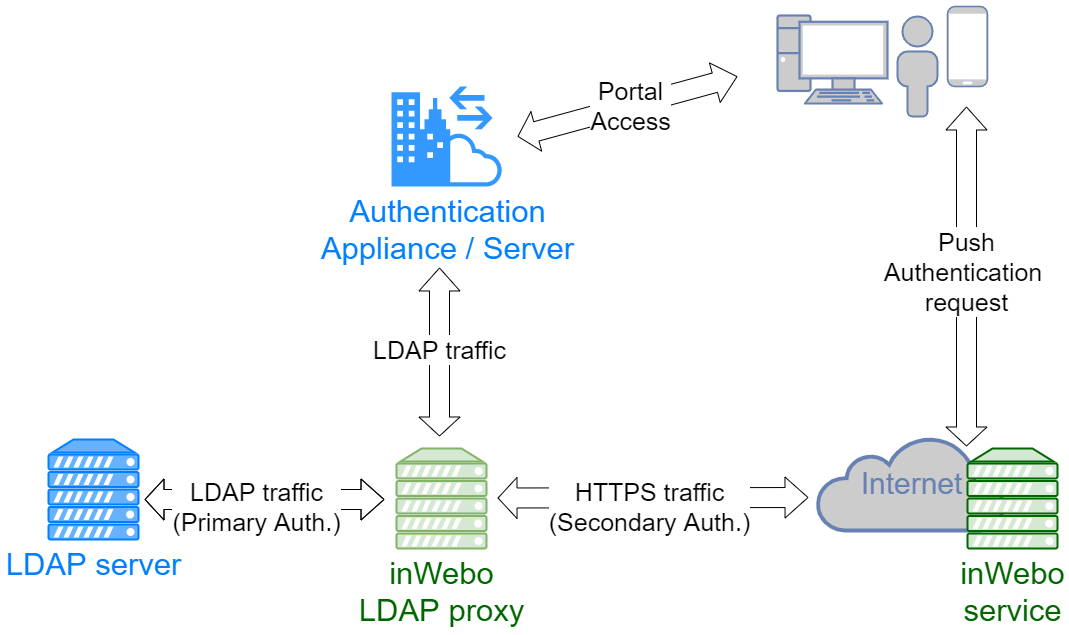
The TrustBuilder MFA LDAP proxy allows you to add strong authentication via the TrustBuilder service.
Its role is to transmit the LDAP requests to the LDAP server. When a Bind request from the LDAP server is returned successfully, a PUSH request is sent to the TrustBuilder server. The user is then prompted to authenticate (PIN code, fingerprint, etc) on his previously registered device.
If the authentication is successful, the LDAP proxy finalizes the Bind request and the user is authenticated.
Prerequisites
Infrastructure
The machine hosting the proxy must have:
Access to the LDAP server that will be connected to the TrustBuilder proxy
Internet access to reach the TrustBuilder MFA API
Software
Windows or Linux
64-bit environment
Java 8 64 bits for the version without JRE or OpenJDK 8 64 bits
For LDAPS / SSL
.P12 certificate and passphrase from local Authority
Installation
Install the TrustBuilder LDAP Proxy on a server reachable from your LDAP server.
For Linux operating systems
Retrieve the Linux version: proxy-ldap-packaging-X.Y.Z-linux64.tar.gz
Unpack the archive
Create the config/config.properties file from the config_to_be_completed.properties file
Complete the config/config.properties file (see below)
Start the proxy:
for version using the JRE installed on the system:
POWERSHELLbin/run.shfor version using built-in JRE:
POWERSHELLbin/run_standalone.sh
Others installation options:
For Windows operating systems
Retrieve the Windows version: proxy-ldap-packaging-X.Y.Z-win64.zip
Unpack the archive
Create the config/config.properties file from the config_to_be_completed.properties file
Complete the config/config.properties file (see below)
Start the proxy
Version using the JRE installed on the system:
VBbin/run.batVersion using the built-in JRE:
VBbin/run_standalone.bat
Others installation options:
Configuration
Summary of configuration items to modify
Basic TrustBuilder LDAP Proxy configuration
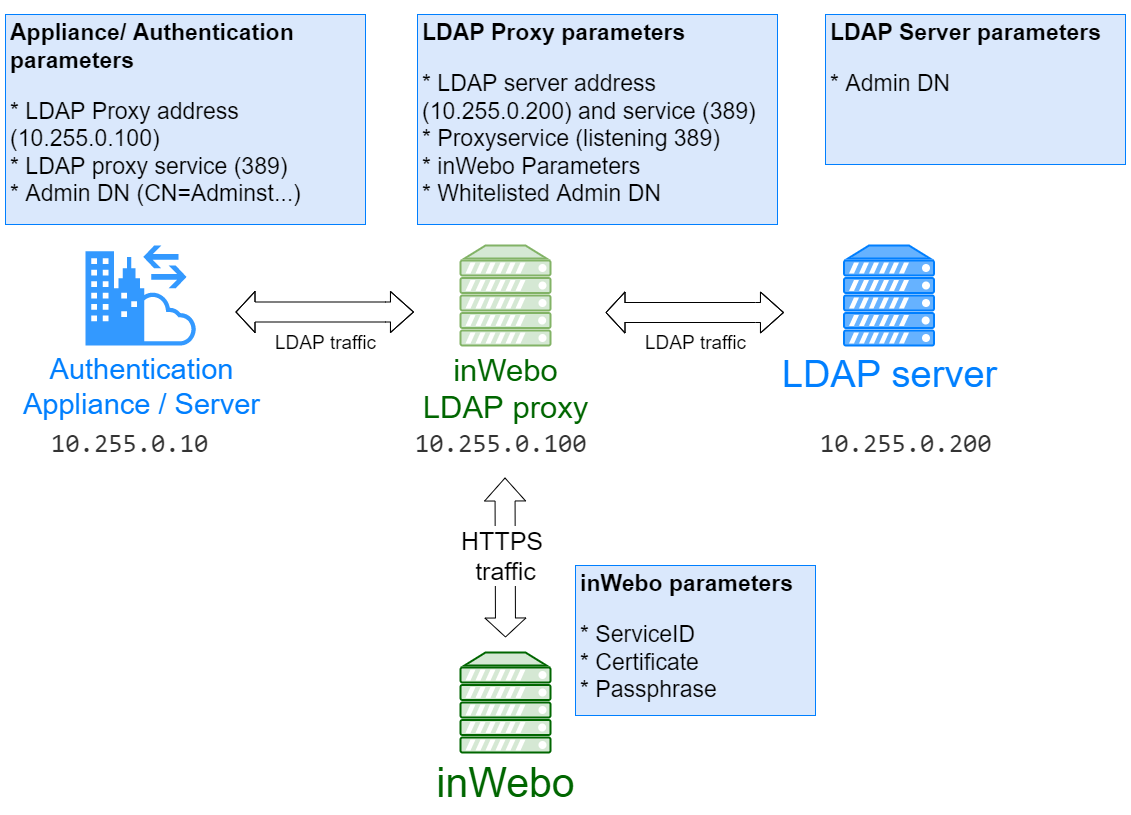
To configure the TrustBuilder LDAP Proxy, you should edit the configuration file (config.properties). The following table lists the required parameters and their values for a minimal configuration.
Parameters | Value | Description |
|---|---|---|
ldap.proxy.port | 389 | the service number of the proxy LDAP is listening to accept requests/ default |
ldap.host | LDAPServ.domain.test | IP address or Name of the LDAP server to send the request to |
ldap.port | 389 | the service number of the proxy LDAP is listening to accept requests/ default |
MyserviceID | your TrustBuilder service ID | |
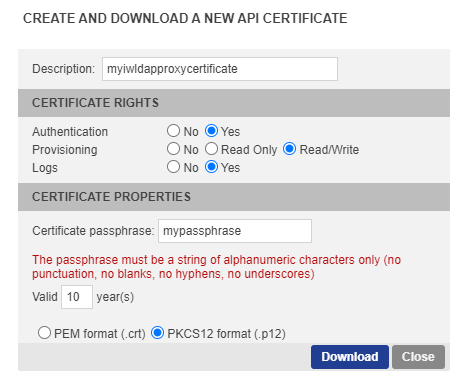
inwebo.service.certificate.path | ./proxyLDAP/inWebo_Certificate12 | the path of the TrustBuilder P12 certificate generated by your Administration console |
inwebo.service.certificate.passphrase | mypassphrase | the passphrase of the TrustBuilder certificate |
Configure your LDAP authentication
Depending on your integration, you will have to configure some settings to redirect the authentication requests to the TrustBuilder LDAP Proxy, instead of LDAP server.
The TrustBuilder LDAP Proxy’s role is to transmit the LDAP requests to the LDAP server. When a Bind request from the LDAP server is returned successfully, an additional authentication request will be sent in HTTPS to the TrustBuilder platform. This additional request is based on the user attribute defined in the inWebo LDAP Proxy configuration and retrieved from the user profile (uid, cn, samAccount, userPrincipleName)
Creating the LDAP credentials (DN) for Binding requests on LDAP server
To bind the LDAP proxy to the target LDAP server it is recommended to indicate or even create a whitelisted DN/Account used to search the LDAP.
ex: CN=ReadOnly,CN=Users,DC=domain,DC=test
This profile will be used as credentials with the LDAP and should not trigger inWebo push authentication each time you send a request to the LDAP server.
Whitelisting the LDAP credentials (DN) in the Configuration.properties file
ldap.proxy.whitelist.dn=CN=ReadOnly,CN=Users,DC=domain,DC=test
This configuration should be replicated on the Appliance/authentication server that will send the request to the inWebo LDAP proxy
Modifying the Appliance / authentication portal to send requests to your LDAP proxy
When configuring the LDAP server on your Appliance / Authentication portal, if an existing configuration already exists to authenticate on the LDAP server, you can duplicate and only replace the IP Address by the address of the LDAP proxy.
Be sure to verify that the LDAP Credentials (DN) / used by this appliance are whitelisted on the LDAP proxy.
Creating the Appliance / authentication portal configuration to send request to your LDAP proxy
If there is no existing profile, you have to indicate the following information:
you have to indicate a new LDAP authentication server:
the IP address of the LDAP proxythe LDAP proxy service number (as indicated previously)
the Base DN of the LDAP server ex: DC=domain,DC=test
the group DN of the LDAP users if existing ex: CN=inWebo,OU=New_York,
the LDAP credentials DN used previously (ldap.proxy.whitelist.dn) CN=ReadOnly,CN=Users,DC=domain,DC=test
with the corresponding password
Testing LDAP Proxy authentication
Run the following command line to test the push Authentication of an inWebo login for your service and see if you are correctly notified with the current inWebo configuration (serviceID, inWebo Certificate, Passphrase).
included for Linux and Windows
run_standalone -doPush <login_inWebo>Troubleshooting LDAP Proxy configuration
Run the following command line to check if the LDAP configuration and the Bind command are successful
included for Linux and Windows
run_standalone -validateConfiguration <DN>For example: run_standalone -validateConfiguration CN=Administrator,CN=Users,DC=Domain,DC=test
Managing simultaneous push requests
ldap.proxy.max.simultaneous.push
The maximum number of simultaneous push requests that can handle the LDAP proxy. This value must be greater than or equal to 1. The default value is 100.
Microsoft Active Directory group configuration
If you wish to activate inWebo MFA only for a subset of your Microsoft Active Directory users (a.k.a. group) you must use either of these group configurations.
Both are valid because MS AD provide by default both group configurations. Choose the one which is the more suitable for you.
# sAMAccountName is typically use for AD, other possibility is cn
# This will be matched with the user “login” (mandatory today) field within inWebo tenant
# to be noted, ldapproxy default (uid) will not work with MS AD
ldap.proxy.login.attribute=sAMAccountName
# group DN for which members will be required to authenticate with inWebo (other users will not use MFA)
# /!\ Change value
ldap.proxy.do.step.up.group.base.dn=CN=<inWebo_group>,DC=<domain>,DC=<tld>
# Choose group membership within the user attributes, with memberOf attribute
ldap.proxy.do.step.up.by.type=user
# LDAP attribute for user memberOf
ldap.proxy.do.step.up.lookup.ismemberof.attribute=memberOfor
Note here that there is an additional mandatory setting ldap.proxy.do.step.up.filter.group.object.class=group
# sAMAccountName is typically use for AD, other possibility is cn
# This will be matched with the user “login” (mandatory today) field within inWebo tenant
# to be noted, ldapproxy default (uid) will not work with MS AD
ldap.proxy.login.attribute=sAMAccountName
# group DN for which members will be required to authenticate with inWebo (other users will not use MFA)
# /!\ Change value
ldap.proxy.do.step.up.group.base.dn=CN=<inWebo_group>,DC=<domain>,DC=<tld>
# Choose group membership with group DN entry
ldap.proxy.do.step.up.by.type=group
# LDAP attribute for group members within the DN group entry
ldap.proxy.do.step.up.lookup.member.attribute=member
# LDAP objectClass attribute used to define a group within MS AD
# to be noted, ldapproxy default (group) will not work with MS AD
ldap.proxy.do.step.up.filter.group.object.class=groupAdvanced parameters for inWebo LDAP Proxy
In the LDAP proxy configuration section, you can set additional parameters.
If you need help using the advanced parameters, please contact our inWebo support team.
The config.properties file
The following settings are in the config / config.properties file.
The config / config.properties file contains all the LDAP Proxy Configuration settings.
Integration examples
Here are some inWebo documentations that refer to third-party integration, using inWebo LDAP proxy.