inWebo LDAP Proxy v1.3.0
Release note 1.3 (November 27, 2020)
Hot fix LDAP Proxy
Support of TLSv1.2
Adding a LDAP server connection timeout
Management of expired AD passwords
Description
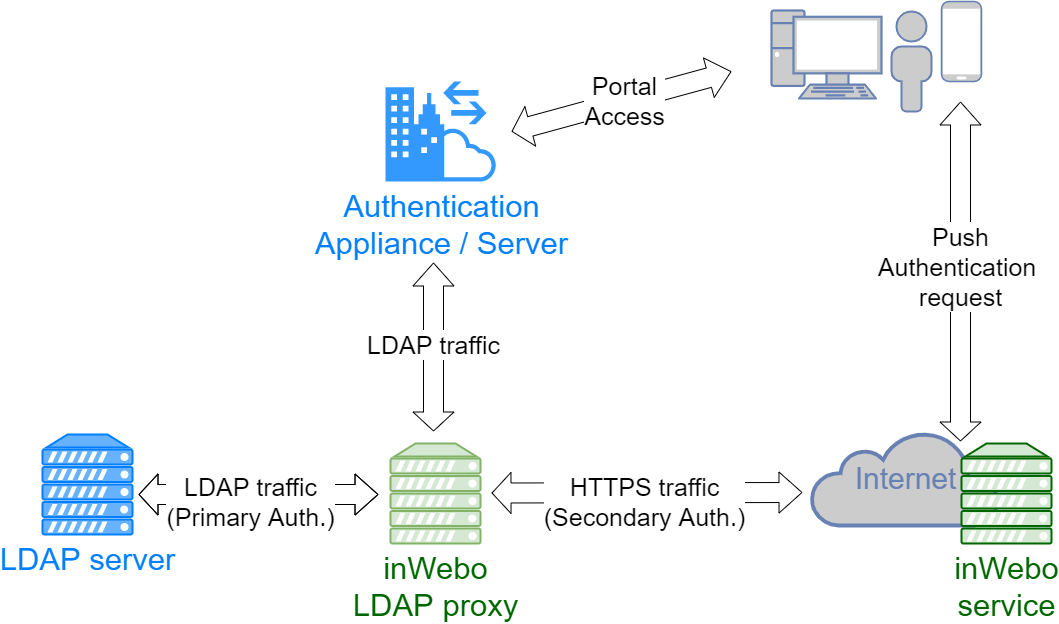
The inWebo LDAP proxy allows you to add strong authentication via the InWebo service.
Its role is to transmit the LDAP requests to the LDAP server. When a Bind request from the LDAP server is returned successfully, a PUSH request is sent to the InWebo server. The user is then prompted to authenticate (PIN code, fingerprint, etc) on his previously registered device.
If the authentication is successful, the LDAP proxy finalizes the Bind request and the user is authenticated.
Prerequisite
Infrastructure
The machine hosting the proxy must have:
Access to the LDAP server that will be connected to the inWebo proxy
Internet access to reach the InWebo API
Software
Windows or Linux
64-bit environment
Java 8 64 bits for the version without JRE or OpenJDK 8 64 bits
For LDAPS / SSL
.P12 certificate and passphrase from local Authority
Installation
For Linux operating systems
Retrieve the Linux version: proxy-ldap-packaging-X.Y.Z-linux64.tar.gz
Unpack the archive
Create the config/config.properties file from the config_to_be_completed.properties file
Complete the config/config.properties file (see below)
Start the proxy
Version using the JRE installed on the system
bin/run.shVersion using built-in JRE
bin/run_standalone.shinWebo proxy service start and stop
If your LDAP proxy listens for services numbered under 1024, you must start the proxy service with a root / administrator user.
Launching the Proxy service in background mode
sudo ./run_standalone.sh &Stopping the Proxy service
sudo ./stop.shProxy installation as a Linux service (requires administrator rights)
Edit bin/iw_ldap_proxy by replacing
@iw_ldap_proxy_installation_dir@ by the path of the installation directory
@iw_ldap_proxy_user@ by the user who runs the program
Installation
BASHsudo cp bin/iw_ldap_proxy /etc/init.d/Start the proxy
BASHsudo /etc/init.d/iw_ldap_proxy startStop the proxy
BASHsudo /etc/init.d/iw_ldap_proxy stop
For Windows operating systems
Retrieve the Windows version: proxy-ldap-packaging-X.Y.Z-win64.zip
Unpack the archive
Create the config/config.properties file from the config_to_be_completed.properties file
Complete the config/config.properties file (see below)
Start the proxy
Version using the JRE installed on the system
bin/run.bat Version using the built-in JRE
bin/run_standalone.batProxy installation as a Windows service (requires administrator rights)
Prerequisites:
.NET Framework 4.0
Installation
bin\ldap_proxy_service.exe installService start
sc start "inWebo LDAP proxy"Service stop
sc stop "inWebo LDAP proxy"Uninstalling the service
bin\ldap_proxy_service.exe uninstallTests and troubleshooting inWebo LDAP Proxy Configuration
2 additional commands are included for Linux and Windows:
Testing Push and inWebo certificate in command line
run_standalone -doPush <login_inWebo>Allows you to test directly the push Authentication of an inWebo login for your service and see if you are correctly notified with the current inWebo configuration (serviceID, inWebo Certificate, Passphrase)
run_standalone -validateConfiguration <DN>(ex: run_standalone -validateConfiguration CN=Administrator,CN=Users,DC=Domain,DC=test)will allow you to test if the LDAP configuration and the Bind command are successful
How to configure your LDAP authentication
This application is used to transfer LDAP search/authentication request to the real authentication LDAP and if accepted it will send an additional authentication request in HTTPS to the inWebo platform.
This additional request is based on the user attribute defined in the proxy LDAP configuration and retrieved from the user profile (uid, cn, samAccount, userPrincipleName)
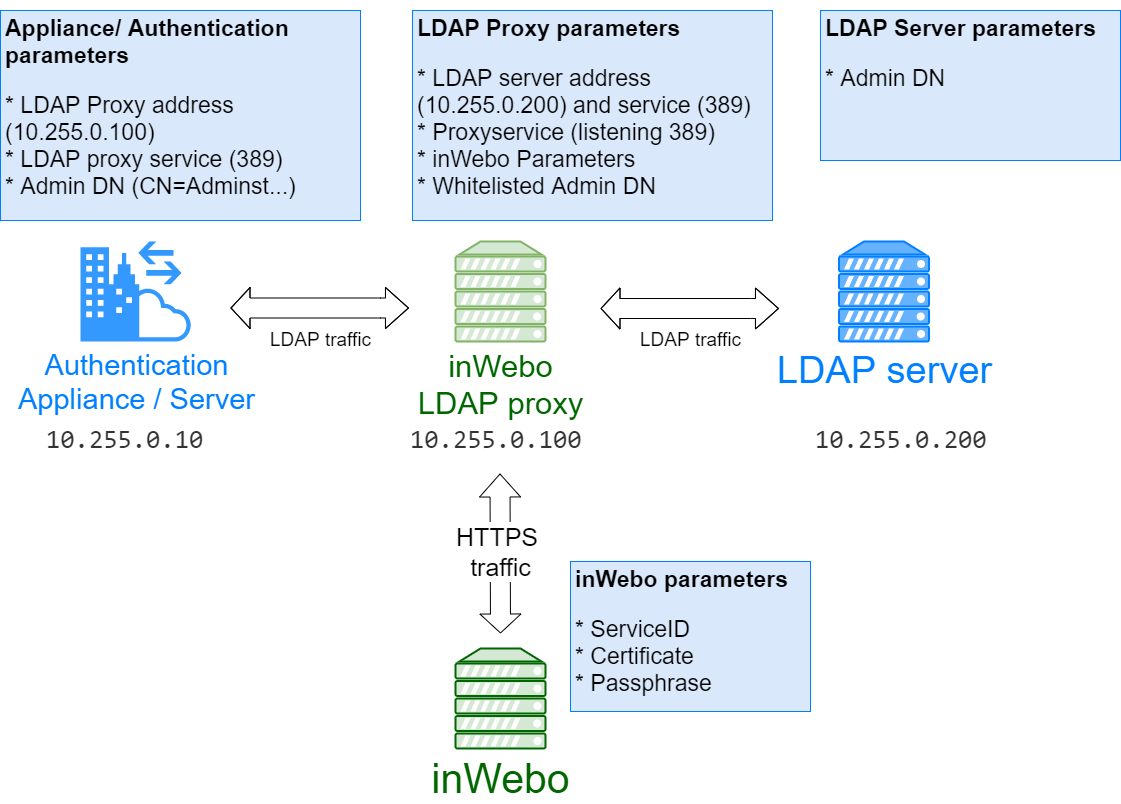
Creating the LDAP credentials (DN) for Binding requests on LDAP server
To bind the LDAPproxy to the target LDAP server it is recommended to indicate or even create a whitelisted DN/Account used to search the LDAP.
ex: CN=ReadOnly,CN=Users,DC=domain,DC=test
This profile will be used as credentials with the LDAP and should not trigger inWebo push authentication each time you send a request tio the LDAP server.
Modifying Configuration.properties file of your LDAP proxy / Minimal Configuration
ldap.proxy.port=389 (the service number of the proxy LDAP is listening to accept requests/ default )
ldap.host=LDAPServ.domain.test (IP address or Name of the LDAP server to send the request to)
ldap.port=389 (the service number of the proxy LDAP is listening to accept requests/ default )
inwebo.service.id=XXXX ( your inWebo service ID)
inwebo.service.certificate.path=C:\ProxyLDAP\inWebo_Certificate12 or./proxyLDAP/inWebo_Certificate12 (the path of the inWebo P12 certificate generated by your inWebo Administration console)
inwebo.service.certificate.passphrase=PASSPHRASE (the password/passphrase of the inWebo certificate)
Whitelisting the LDAP credentials (DN) in the Configuration.properties
ldap.proxy.whitelist.dn=CN=ReadOnly,CN=Users,DC=domain,DC=test
This configuration should be replicated on the Appliance/authentication server that will send the request to the LDAP proxy
Modifying the Appliance / authentication portal to send requests to your LDAP proxy
When configuring the LDAP server on your Appliance / Authentication portal
if an existing configuration already exists to authenticate on the LDAP server, you can duplicate and only replace the IP Address by the address of the LDAP proxy.
Be sure to verify that the LDAP Credentials (DN) / used by this appliance are whitelisted on the LDAP proxy.
Creating the Appliance / authentication portal configuration to send request to your LDAP proxy
if there is no existing profile, you have to indicate the following information:
you have to indicate a new LDAP authentication server:
the IP address of the LDAP proxythe LDAP proxy service number (as indicated previously)
the Base DN of the LDAP server ex: DC=domain,DC=test
the group DN of the LDAP users if existing ex: CN=inWebo,OU=New_York,
the LDAP credentials DN used previously (ldap.proxy.whitelist.dn) CN=ReadOnly,CN=Users,DC=domain,DC=test
with the corresponding password
Summary of configuration items to modify
Additional parameters for inWebo LDAP Proxy v1.3.0
In the LDAP proxy configuration section, you can now set additional parameters
Transport Layer Security (TLS) Parameters
For sending requests to the LDAP proxy: ldap.proxy.cipher.protocol
and when forwarding the request to the LDAP: proxy.cipher.protocol
Possible values:
Automatic choice of JVM: "TLS"
Protocol TLS v1: TLSv1
Protocol TLS v1.1: TLSv1.1
Protocol TLS v1.2: TLSv1.2
Managing requests timeouts
You can now set timeout values for requests
For the Request timeout between the LDAP proxy and the LDAP server
Value in ms. Default 0 ( no timeout )
Setting: ldap.proxy.request.timeout
If a response is not received from the Directory Server within the timeout period, then the operation will be abandoned and an Exception error result returned.
A timeout setting of 0 disables operation timeout limits
For the Request timeout between the LDAP client and the LDAP proxy
Value in ms. Default 10000 ( 10sc )
Setting: ldap.proxy.connect.timeout
If a connection is not established within the timeout period (incl. SSL negotiation, initial bind request, and/or heart-beat), then an Exception error result will be returned.
The default operation timeout is 10 seconds and a timeout setting of 0 causes the OS connect timeout to be used.
When the timeout value is exceeded
An error is returned when the connection failed
"Authentication to LDAP failed : < information>"The error is logged in the LDAP Proxy log file
LDAP proxy Configuration settings
The following settings are in the config / config.properties file
LDAP PROXY CONFIGURATION SECTION
LDAP proxy's own IP addresses and service
Listening IP addresses, used by the LDAP proxy (List of IP/hostname separated by ";" - the LDAP proxy is listening to all registered IP addresses by default)
#ldap.proxy.addresses=
# Listening port for the LDAP proxy
ldap.proxy.port=389
# Listening port for the LDAP proxy to handle LDAPS requests
#ldap.proxy.ssl.port=636
IP addresses and service of the targeted LDAP server
# LDAP server address/hostname
ldap.host=
# LDAP server port
# Required if ldap.proxy.port is set
ldap.port=389
# LDAPS server port
#ldap.ssl.port=636
LDAPS configuration and local Keystore
# full path to a p12 certificate associated with the LDAP
#ldap.proxy.ssl.certificate.path=
# LDAP certificate passphrase
#ldap.proxy.ssl.certificate.passphrase=
# Mode of server certificate verification
# jvm by default
# jvm : use the JVM keystore
# none : trust all server certificates
# keystore : use a specific keystore defineby ldap.ssl.certificate.keystore and ldap.ssl.certificate.passphrase
#ldap.ssl.certificate.verification.mode=
# The path of the keystore to use when ldap.ssl.certificate.verification.mode=keystore
#ldap.ssl.certificate.keystore.path=
# The keystore pass associated to ldap.ssl.certificate.keystore.path
#ldap.ssl.certificate.keystore.passphrase=
Transport Layer Security (TLS) Parameters (new for 1.3)
# Protocol used for requesting the LDAP proxy
# default is TLS
#ldap.proxy.cipher.protocol=
# Protocol used by the LDAP proxy to request the LDAP
# default is TLSv1
#proxy.cipher.protocol=
Managing requests timeouts (new for 1.3)
# Request timeout between proxy and LDAP server ( in ms )
# default 0 ( no timeout )
#ldap.proxy.request.timeout=
# Timeout of proxy requests ( in ms )
# default 10000 ( 10sc )
#ldap.proxy.connect.timeout=
INWEBO SERVICE CONFIGURATION SECTION
Base configuration (service ID, certificate path and passphrase)
# InWebo service ID
inwebo.service.id=
# full path to the p12 certificate associated with the InWebo service
inwebo.service.certificate.path=
# inWebo certificate passphrase
inwebo.service.certificate.passphrase=
LDAP Attribute on the requested User profile, used to match with the inWebo login (uid, cn, samAccount, userPrincipalName..)
can be different from initial login request
# LDAP attribute for user login (will be matched with InWebo login), # uid by default
#ldap.proxy.login.attribute=
LDAP Group, DN, conditions for inWebo Authentication
# Condition to authenticate users with InWebo
# all by default
# all : all user will be authenticated with inWebo
# none : no user will be authenticated with inWebo (transparent)
# user : user group membership. Based on the group list the user is member of
# group : user group membership. Based on the group member list
#ldap.proxy.do.step.up.by.type=all
# LDAP group DN for which members will be required to authenticate with inWebo. Required if ldap.proxy.do.step.up.by.type is set to "user" or "group"
#ldap.proxy.do.step.up.group.base.dn=
# LDAP attribute for group members. Required when ldap.proxy.do.step.up.by.type = group
# member by default
#ldap.proxy.do.step.up.lookup.member.attribute=
# LDAP attribute for group list. Required when ldap.proxy.do.step.up.by.type = user
# isMemberOf by default. Use memberOf for AD
#ldap.proxy.do.step.up.lookup.ismemberof.attribute=
# LDAP objectClass attribute used to define a group
# groupOfNames by default
#ldap.proxy.do.step.up.filter.group.object.class=
# LDAP objectClass attribute used to define a user
# person by default
#ldap.proxy.do.step.up.filter.user.object.class=
Whitelisting of Admin and credentials used to bind and search
# Bypass inWebo authentification for a list of users (usefull for technical accounts)
# DN list separated by ";"
#ldap.proxy.whitelist.dn=
# 16 characters key used to cipher logins
# No cipher by default
#inwebo.cipher.aes.secret.key=
INWEBO API CONFIGURATION SECTION
additional configuration for on premise version and proxy support
# InWebo API URL
# https://api.myinwebo.com/FS by default
#inwebo.base.url=
# Force ldap-proxy to contact inWebo through an http or https proxy
# HTTP proxy host used to call InWebo
# No HTTP proxy by default
#inwebo.proxy.host=hostname_or_ip
# HTTP proxy port
#inwebo.proxy.port=port
# Use https to proxy
# false by default - http only (http://hostname:port)
# true - https only (https://hostname:port)
#inwebo.proxy.https=true
# HTTP proxy login - option
#inwebo.proxy.username=proxy_user_login
# HTTP proxy password - option
#inwebo.proxy.password=proxy_user_password