inWebo LDAP Proxy v1.1.0
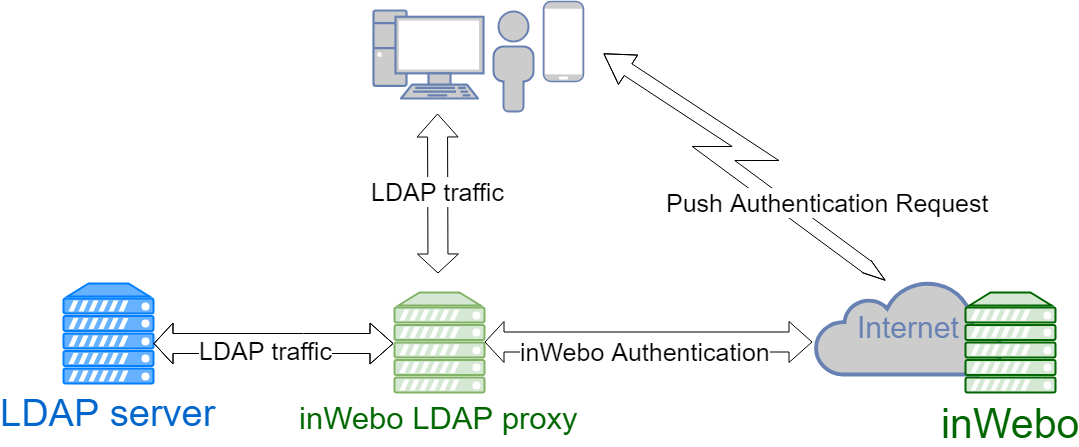
The inWebo LDAP proxy allows you to add strong authentication via the InWebo service.
Its role is to transmit the LDAP requests to the LDAP server. When a Bind request from the LDAP server is returned successfully, a PUSH request is sent to the InWebo server. The user is then prompted to authenticate (PIN code, fingerprint, etc) on his previously registered device.
If the PIN is correct, the LDAP proxy finalizes the Bind request and the user is authenticated.
Prerequisite
Infrastructure
The machine hosting the proxy must have:
Access to the LDAP server that will need to be synchronized with the inWebo proxy
Internet access to reach the InWebo API
Software
Windows or Linux
64-bit environment
JAVA 8 64 bits for the version without JRE
For LDAPS / SSL
.P12 certificate and passphrase from LDAP server
Installation
For Linux operating systems
Retrieve the Linux version: proxy-ldap-packaging-X.Y.Z-linux64.tar.gz
Unpack the archive
Create the config/config.properties file from the config_to_be_completed.properties file
Complete the config/config.properties file (see below)
Start the proxy
Version using the JRE installed on the system
bin/run.shVersion using built-in JRE
bin/run_standalone.shinWebo proxy service start and stop
If your LDAP proxy listens for services numbered under 1024, you must start the proxy service with a root / administrator user.
Lauching the Proxy service in background mode
sudo ./run_standalone.sh &Stopping the Proxy service
sudo ./stop.shProxy installation as a Linux service (requires administrator rights)
Edit bin/iw_ldap_proxy by replacing
@iw_ldap_proxy_installation_dir@ by the path of the installation directory
@iw_ldap_proxy_user@ by the user who runs the program
Installation
BASHsudo cp bin/iw_ldap_proxy /etc/init.d/Start the proxy
BASHsudo /etc/init.d/iw_ldap_proxy startStop the proxy
BASHsudo /etc/init.d/iw_ldap_proxy stop
For Windows operating systems
Retrieve the Windows version: proxy-ldap-packaging-X.Y.Z-win64.zip
Unpack the archive
Create the config/config.properties file from the config_to_be_completed.properties file
Complete the config/config.properties file (see below)
Start the proxy
Version using the JRE installed on the system
bin/run.bat Version using the built-in JRE
bin/run_standalone.batProxy installation as a Windows service (requires administrator rights)
Prerequisites:
.NET Framework 4.0
Installation
bin\ldap_proxy_service.exe installService start
sc start "inWebo LDAP proxy"Service stop
sc stop "inWebo LDAP proxy"Uninstalling the service
bin\ldap_proxy_service.exe uninstallConfiguration
The following settings are in the config / config.properties file
LDAP Configuration
ldap.proxy.ssl.certificate.path=full path to a p12 certificate associated with the LDAP
ldap.proxy.ssl.certificate.passphrase=LDAP certificate passphrase
ldap.ssl.certificate.verification.mode=# Mode of server certificate verification
# jvm by default
# jvm: use the JVM keystore
# none: trust all server certificates
# keystore: use a specific keystore defined by ldap.ssl.certificate.keystore and ldap.ssl.certificate.passphrase
ldap.ssl.certificate.keystore.path=The path of the keystore to use when ldap.ssl.certificate.verification.mode=keystore
ldap.ssl.certificate.keystore.passphrase=The keystore pass associated to ldap.ssl.certificate.keystore
ldap.proxy.addresses : list of IP addresses, separated by ";", on which the LDAP proxy will listen for LDAP queries. By default, the proxy listens on the address ":: 0" (Optional)
ldap.host: the LDAP server address (Required)
ldap.proxy.port or ldap.port: the proxy port and the LDAP port to use to support LDAP requests.
ldap.proxy.ssl.port or ldap.ssl.port: the proxy port and the LDAP port to use to support LDAPS requests.
inwebo.service.id: the inWebo service number that will be associated with InWebo authentication (Required)
inwebo.service.certificate.path: The full path to the p12 certificate associated of the InWebo service (Required)
inwebo.service.certificate.passphrase: The certificate passphrase associated with the InWebo service (Required)
ldap.proxy.login.attribute: The name of the LDAP attribute containing the InWebo login. It is set to "uid" by default (possibly the UPN - UserPrincipalName)
ldap.proxy.do.step.up.by.type: Allow to condition the authentication via InWebo:
user: searches the LDAP from the user if he is a member of the group that allows authentication via InWebo
group: search LDAP from members of the group that allows authentication via InWebo
all: authentication via InWebo for all users
none: authentication via InWebo for no users
Set to "all" by default
ldap.proxy.do.step.up.group.base.dn: The group DN in the LDAP containing users for whom authentication via InWebo will be enabled. Required if ldap.proxy.do.step.up.by.type is filled in to "user" or "group"
ldap.proxy.do.step.up.lookup.member.attribute: The name of the LDAP attribute that defines a member. This parameter is required when ldap.proxy.do.step.up.by.type = group. Set to "member" by default
ldap.proxy.do.step.up.lookup.ismemberof.attribute: The name of the LDAP attribute that defines group membership. This parameter is required when ldap.proxy.do.step.up.by.type = user. Fixed to "isMemberOf" by default
ldap.proxy.do.step.up.filter.group.object.class: The value of the LDAP objectClass attribute defining a group. Required, set to "groupOfNames" by default
ldap.proxy.do.step.up.filter.user.object.class: The value of the LDAP objectClass attribute that defines a user. Required, set to "person" by default
inwebo.cipher.aes.secret.key: 16 characters Key to encrypt the login. Encryption is not enabled by default
ldap.proxy.whitelist.dn : DN list, separated by ";", for which there will be no InWebo authentication, used as technical accounts to operate BIND requests. (i.e: CN=Administrator,CN=Users,DC=domain,DC=com;CN=ReadOnly,CN=Users,DC=domain,DC=com; )
inWebo HTTP API configuration
inwebo.base.url: InWebo API URL
inwebo.proxy.host: HTTP proxy IP or hostname used to make calls to the InWebo API. There is no default HTTP proxy
inwebo.proxy.port: HTTP proxy port to use
inwebo.proxy.https: Boolean which allows to switch to HTTPS mode. The possible values are "true" or "false". Set to false by default (HTTP)
inwebo.proxy.username: Login associated with the HTTP proxy (do not use realm\username for NTLM, instead use the username from a domain joined server OR username@domain)
inwebo.proxy.password: Associated password