Citrix Netscaler - SAML integration
Prerequisite
A configured Netscaler Gateway Virtual server with a valid certificate
You have to make sure that your Netscaler Gateway Virtual Server has a valid certificate installed
Netscaler > Virtual Servers > Edit your Gateway Virtual Server
in the "Certificate" section verify the existing certificate or bind a new one for this server if there is no certificate indicated.
Creating the inWebo SAML connector
In your inWebo service, go to the "Secures Sites" tab, select "Add a connector of type" SAML 2.0.
In your SAML connector properties :
Download the inWebo Idp SAML 2.0 metadata in XML format
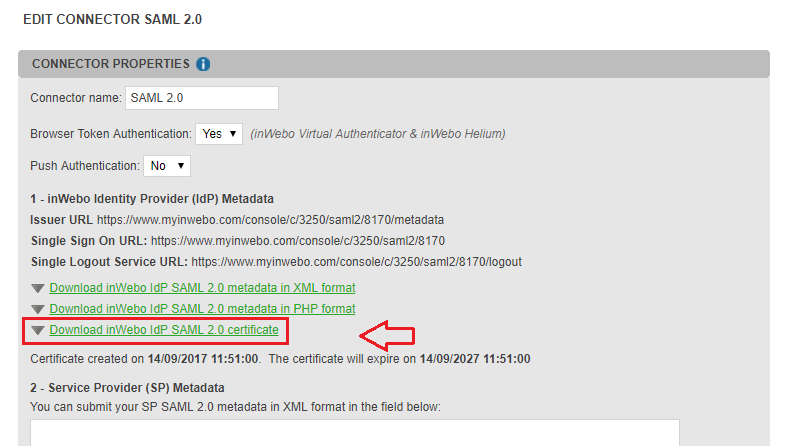
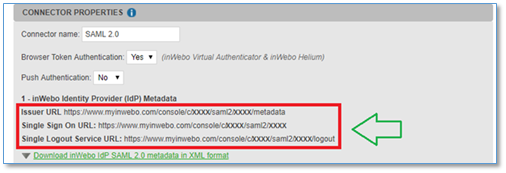
After downloading your inWebo IDP SAML certificate, copy the following information needed by your Netscaler configuration :
Identity Provider Entity Identifier (issuer URL) “https://www.myinwebo.com/console/c/XXXXXX/saml2/XXXXXX/metadata”
Single Sign On URL – https://www.myinwebo.com/console/c/XXXXXX/saml2/XXXXXX/”
Single Logout URL – https://www.myinwebo.com/console/c/XXXXXX/saml2/XXXXXX/logout”
You should see the following SAML 2.0 connector information in the administration console:
Netscaler Configuration
Creating a new Authentication SAML Policy
In the configuration utility, on the Configuration tab, expand Netscaler Gateway > Policies > Authentication.
Click "SAML", and then in the details pane, on the Policies tab, click Add .
In the Create Authentication Policy dialog box, in Name, type a name for the policy.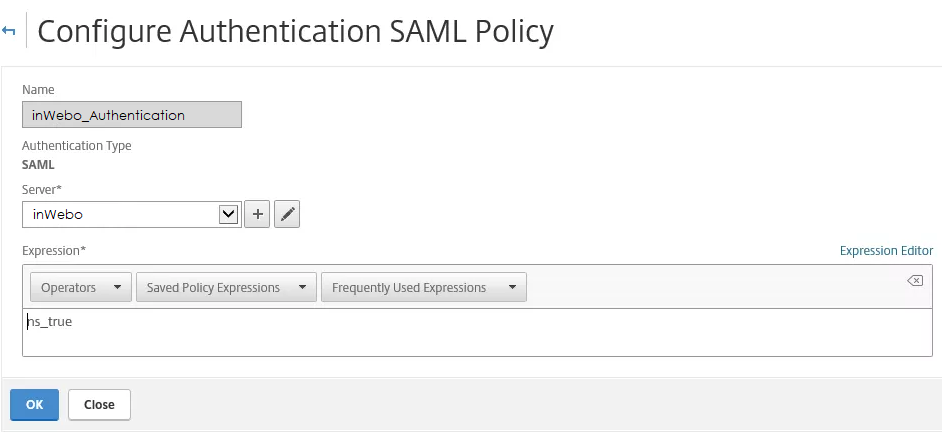
Put "ns_true" as the expression as this policy is to be used for all authentication.
Creating a new Authentication SAML Server
Next to Server, click New.(+)
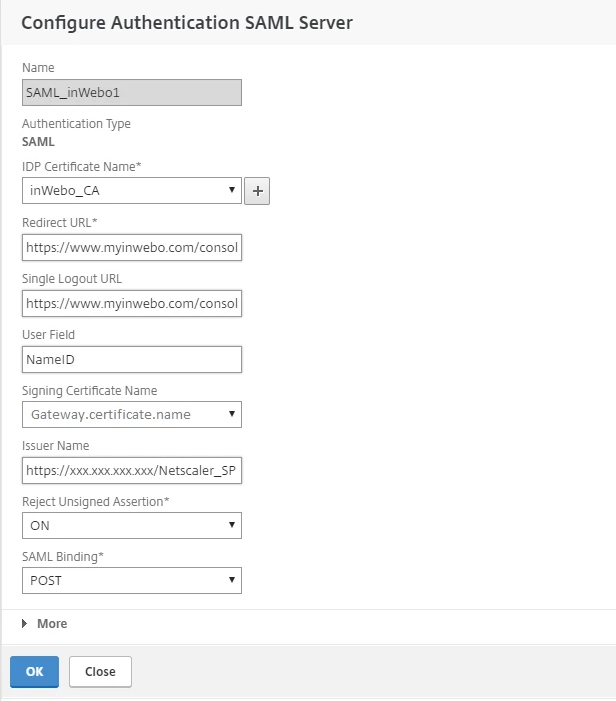
In the Name field, indicate a name for the new server profile.
Fill this page with the following information concerning your inWebo service
Redirect URL: https://www.myinwebo.com/console/c/XXXX/saml2/XXXX
Single Logout URL: https://www.myinwebo.com/console/c/XXXX/saml2/XXXX/logout
User Field: NameID
Issuer Name: https://***Netscaler_IP***/Netscaler_SP (for example)
Reject Unsigned Assertion: ON
SAML Binding : POST
In "IDP Certificate Name", select the private key for the certificate you selected in the Prerequisite section above.
The "Issuer Name" is the fully qualified domain name (FQDN) to which users log on, such as lb.example.com or ng.example.com.
In "Issuer Name", enter the FQDN of the Virtual Server or its IP address.
Click Create twice to save both configuration.
Binding the Authentication SAML Policy to a Netscaler Gateway Virtual Server
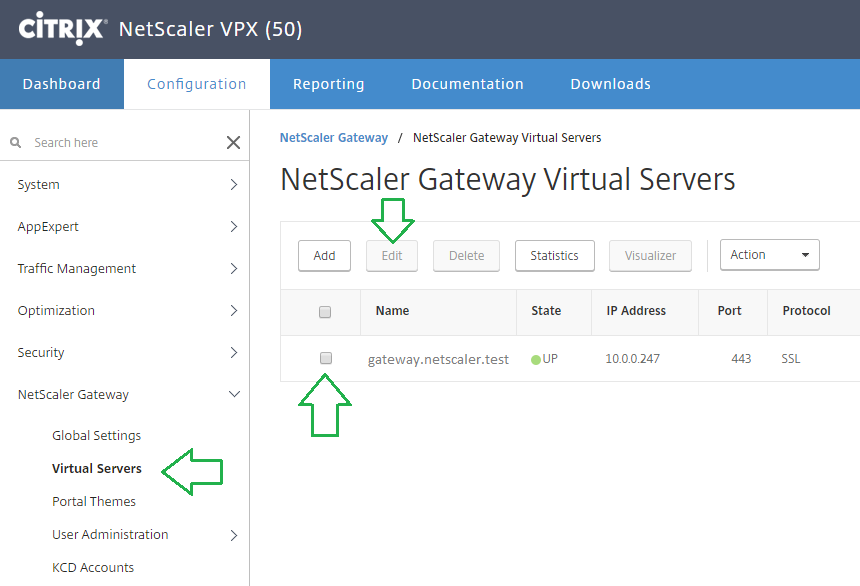
Select the Gateway Virtual Server you want to bind with this Authentication policy.
In the Virtual server Authentication page, select "Basic Authentication" section and click on the Add icon "+"
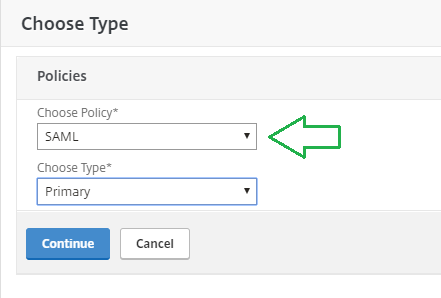
Select SAML as Policy and click "Continue"
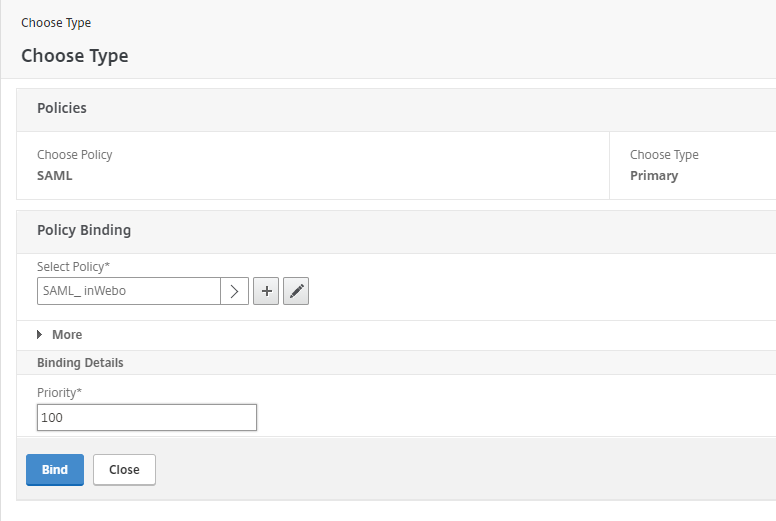
Select the newly created inWebo SAML policy and click "Bind" to apply it for this server.
Constructing the Netscaler SP SAML assertion
SAML assertion sample for a "gateway.netscaler.test" portal.
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" ID="_724200788f8391f96053f72adc628fecc808d099" entityID="https://gateway.netscaler.test">
<md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol urn:oasis:names:tc:SAML:1.1:protocol urn:oasis:names:tc:SAML:1.0:protocol">
<md:Extensions>
<init:RequestInitiator xmlns:init="urn:oasis:names:tc:SAML:profiles:SSO:request-init" Binding="urn:oasis:names:tc:SAML:profiles:SSO:request-init" Location="https://www.myinwebo.com/console/c/XXXX/saml2/XXXX"/>
</md:Extensions>
<md:KeyDescriptor>
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:KeyName>gateway.netscaler.test</ds:KeyName>
<ds:X509Data>
<ds:X509SubjectName>CN=gateway.forserge.test</ds:X509SubjectName>
<ds:X509Certificate>MIIEIzCCA4ygAwIBAgIBADANBgkqhkiG9w0BAQsFADCBqDELMAkGA1UEBhMCVVMx
EzARBgNVBAgTCkNhbGlmb3JuaWExHjAcBgNVBAoTFWdhdGV3YXkuZm9yc2VyZ2Uu
dGVzdDEeMBwGA1UECxMVZ2F0ZXdheS5mb3JzZXJnZS50ZXN0MR4wHAYDVQQDExVn
YXRld2F5LmZvcnNlcmdlLnRlc3QxJDAiBgkqhkiG9w0BCQEWFXN1cHBvcnRAbmV0
c2NhbGVyLmNvbTAeFw0xODA0MjQxNDIwMDhaFw0xOTA0MjQxNDIwMDhaMIGoMQsw
CQYDVQQGEwJVUzETMBEGA1UECBMKQ2FsaWZvcm5pYTEeMBwGA1UEChMVZ2F0ZXdh
eS5mb3JzZXJnZS50ZXN0MR4wHAYDVQQLExVnYXRld2F5LmZvcnNlcmdlLnRlc3Qx
HjAcBgNVBAMTFWdhdGV3YXkuZm9yc2VyZ2UudGVzdDEkMCIGCSqGSIb3DQEJARYV
c3VwcG9ydEBuZXRzY2FsZXIuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKB
gQCtzZLd9NKwX1on59jMGfxQtSkUjSVQfTkuiyK3fs9Ys1QcuDZgfj/uHeo920/+
SiHulFARNJ9Bj5IRrzhGmRXD4OWT+fz0nHid9EA2M6kAfytWwBhPDVDzVCd4NYsQ
q2Oz4ZDI/r4xqxNfLEQIZkRegvHFFffEI5YDSmt82J9HQQIDAQABo4IBWTCCAVUw
HQYDVR0OBBYEFOrto822q8Q/MRVxyL8WguWx8KyEMIHVBgNVHSMEgc0wgcqAFOrt
o822q8Q/MRVxyL8WguWx8KyEoYGupIGrMIGoMQswCQYDVQQGEwJVUzETMBEGA1UE
CBMKQ2FsaWZvcm5pYTEeMBwGA1UEChMVZ2F0ZXdheS5mb3JzZXJnZS50ZXN0MR4w
HAYDVQQLExVnYXRld2F5LmZvcnNlcmdlLnRlc3QxHjAcBgNVBAMTFWdhdGV3YXku
Zm9yc2VyZ2UudGVzdDEkMCIGCSqGSIb3DQEJARYVc3VwcG9ydEBuZXRzY2FsZXIu
Y29tggEAMAwGA1UdEwQFMAMBAf8wCwYDVR0PBAQDAgEGMBEGCWCGSAGG+EIBAQQE
AwIBBjAuBglghkgBhvhCAQ0EIRYfTmV0U2NhbGVyIEdlbmVyYXRlZCBDZXJ0aWZp
Y2F0ZTANBgkqhkiG9w0BAQsFAAOBgQCgKI0bBqJjp8Kg54PZAAzNhqdGwr3OMx64
UP9vOtSFYNS92AVISSP/fQOrH/tcqzwsubr62U4Zx4gQ9EBPkS5DQHKVkkuJMfPy
6KW8mX47KluP7m2zhLODCzrWwD9N+FzBD5xmhCRZEWm+r3ZrjGvhHNUQ51REanxh
ngU0c0Fydg==</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://gateway.netscaler.test/cgi/samlauth" index="0"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>You have to create this assertion with different elements from your own Netscaler configuration.
EntityDescriptor entityID
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" ID="_724200788f8391f96053f72adc628fecc808d099" entityID="https://gateway.netscaler.test">
Indicate the Virtual server HTTPS address
init:RequestInitiator Location
<init:RequestInitiator xmlns:init="urn:oasis:names:tc:SAML:profiles:SSO:request-init" Binding="urn:oasis:names:tc:SAML:profiles:SSO:request-init" Location="https://www.myinwebo.com/console/c/XXXX/saml2/XXXX"/>
Complete with your inWebo service Single Sign On URL ("https://www.myinwebo.com/console/c/XXXX/saml2/XXXX")
ds:KeyName
<ds:KeyName>gateway.netscaler.test</ds:KeyName>
Complete with the Virtual server FQDN
ds:X509SubjectName
<ds:X509SubjectName>CN=gateway.forserge.test</ds:X509SubjectName>
Complete with the Virtual server FQDN
ds:X509Certificate
Navigate to Traffic Management > SSL and select "Manage Certificates / Keys / CSRs"
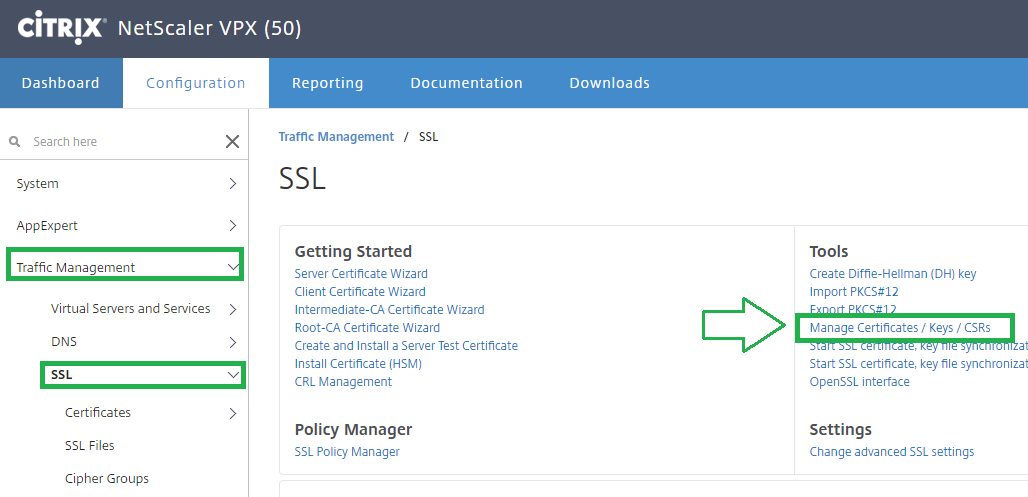
Select the certificate used by your Virtual server:

Select View and copy / paste the content under the ds:X509Certificate section of the SAML assertion
md:AssertionConsumerService Location
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://gateway.netscaler.test/cgi/samlauth" index="0"/>
Indicate the Virtual server HTTPS address completed with /cgi/samlauth ("https://*****virtual_server*****/cgi/samlauth")
Updating the inWebo SAML connector
In your inWebo service, in the "Secures Sites" tab, select the previously created SAML 2.0 connector.
Edit your SAML connector properties and paste the SAML assertion you have constructed.
In the SAML attributes section,
Add a SAML Attribute to map "NameID" with the User login, to transfer this Attribute in the authentication process.
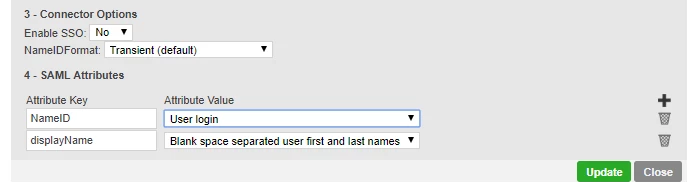
Click the Update button to complete this configuration.
Creating the corresponding SAML 2.0 "Secure Site"
In the inWebo Administration console, in the "Secure Sites" tab
Click on "Add a Secure Site of type..." and select the SAML 2.0 corresponding to your SAML connector" in the first column.

The called URL should correspond to your Nestcaler portal page.
inWebo SAML authentication test
When connecting to the Virtual server protected by the inWebo authentication policy, you'll be redirected to myinwebo.com site for authentication.
On successful authentication you'll be redirected to the Netscaler Unified Gateway and your inWebo login will be displayed