F5 BIG-IP, RADIUS and SAML integrations
This is the procedure to integrate inWebo multi factor authentication service with "F5 BIG-IP " Radius or SAML authentication.
Introduction
In-Webo provides software 2-factor authentication technologies with a « chip & PIN » security level. InWebo tokens can be used on any device (desktop, tablet, smartphone, etc.), without any expertise and in a self-service mode. In-Webo offers a highly available trusted platform, built with Hardware Security Modules (HSM), compatible with your Identity Management systems, which you can implement in SaaS mode, in a matter of hours, with no new infrastructure or investment.
The purpose of this guide is to explain how to use InWebo products with F5 BIG-IP APM (Access Policy Manager).
General Principles
InWebo strong authentication service supports many built-in interfaces such as Radius, SAML 2.0, Web Services API, Google Apps and many more. When working with a network device (firewall, reverse proxy,…) the preferred method is RADIUS. This is what we will explain further in this document.
Architecture is described below:
Users can download and manage InWebo tokens by themselves. In order to get the whole system up and running, your company system administrator only has to:
Configure F5 BIG-IP APM authentication portal with Radius (5 min) or SAML (10 min)
Create an InWebo account (2 min)
Download, install and activate one of InWebo tokens (4 min)
Configure Radius and/or SAML connector in his InWebo account (2 min)
Perform a test authentication (1 min)
Basically, the whole system can be up and running in 15-20 minutes.
Configuring InWebo Radius authentication on a F5 BIG-IG APM
Note: we will take for granted that you already have a F5 BIG-IP device up and running. we also assume that you also have one Access Policy configured
1. InWebo radius connector configuration
Connect to the InWebo administration console https://www.myinwebo.com/console
Go to “Secure Sites” tab
In the “Connectors” part, choose “Radius Push” or “Radius” in the drop-down list of possible connectors
Fill in the “IP Address” field with the IP of the public interface of the F5 APM device (or NAT address if behind a firewall).
Enter a “secret” and keep that secret in mind for a later use in section 2 below. (As a reminder, a shared secret is a text string that serves as a password between.)
Validate your connector configuration by pressing “Update” button.
Any modification made to your radius configuration will be applied within the next 15 minutes.
2. F5 InWebo radius server configuration
You have to configure the F5 system to use InWebo radius pool servers.
Connect to your F5 Administration interface.
Go to MAIN tab > Access Policy > AAA Servers > Radius and clic the (+) sign to add a new server definition
Give it a name in the mandatory corresponding field
In the configuration section, ensure “Authentication” mode is ticked
Use pool must is ticked by default.
Add radius-a.myinwebo.com and radius-b.myinwebo.com as Server Addresses with the Add button. If your F5 device is not able to resolve internet addresses, you'll have to set IP addresses instead of the FQDN. You'll find the InWebo radius servers addresses in your MyInWebo admin console, by editing the Radius connector as explained in section 1.
Fill in the “Secret” text box with the exact same one configured above on your MyInWebo admin console
Clic the “Update” button to validate your configuration.
inWebo Radius server addresses :
Primary: radius-a.myinwebo.com (95.131.139.137)
Secondary: radius-b.myinwebo.com (217.180.130.59)
(See RADIUS integration and redundancy for additional details and configuration)
3. Configuring an access policy to authenticate with the InWebo Radius servers
Note : We assume that you already have at least one Access Profile configured. If not, please refer to your F5 admin guide in order to configure an access profile before you start this task.
When you use the BIG-IP system with Radius authentication, configure an access policy with a Radius Auth box.
On the Main tab, click Access Policy > Access Profiles. The Access Profiles List screen opens.
In the Access Policy column, click the Edit link for the access profile you want to configure to launch the visual policy editor. The visual policy editor opens the access policy in a separate screen.
Click the (+) sign after the login page in the access policy to add a new action item. An Add Item screen opens, listing Predefined Actions that are grouped by General Purpose, Authentication, and so on.
From the Authentication area, select “RADIUS Auth” and click the Add Item button. The Radius properties window opens.
In the Radius Authentication area from the AAA Server list, select the Radius Pool you've just created and click Save. The Access Policy window displays.
If needed, change the Successful rule branch from Deny to Allow and click the Save button.
At the top of the window, click the Apply Access Policy link to apply and activate your changes to this access policy.
Click the Close button to close the visual policy editor.
Your access policy should at least look like this one :
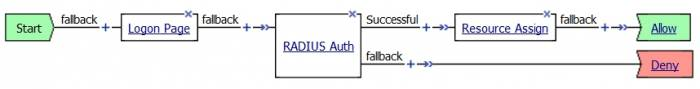
You now have an access policy that should work correctly and use InWebo Radius authentication.
OPTIONAL: Virtual Authenticator integration in the F5 login page
Instead of having to generate manually an OTP with your phone to login through the radius, you may want to integrate InWebo Helium to the F5 login page to authenticate your users. To do so, you have to do this 2 step configuration
Create a Secure Site in your MyInWebo Administration Console, and activate Helium on it
Open your MyInwebo Admin Console
In “Secure Sites” Tab > “Secure Sites”, choose “WebService Connector” or “radius push” in the “Add a Secure Site of type…” drop-down list
Give it a Name
Fill the 'Called Url' field with the URL of your BigIp login page
Click “Automatic Detection” to recognize the form name and login/password field names
If they are not recognized, manually “e1” for 'Form name', “username” for 'Login' and “Password” for 'password.
Click “Add” to add this new site, then close.
Then click the “Browser token activation button” to generate a unique “Bookmark Alias” for that secure site
Copy-paste somewhere the “Bookmark Alias” value for a later use in the next step
That's all for the InWebo part
Next, you need to customize the login page on your F5 device :
Connect to your F5 Administration interface.
Go to MAIN tab > Access Policy > Customization > Advanced
A new window opens, click on the “Edit Mode” button to choose “Advanced”
Under the “Customization Settings”, expand “Access Profiles” with the [+] sign
Expand the profile corresponding to your radius configuration, then expand “Access Policy”, then “Logon Page” twice in order to be able to view/edit “login.inc” file
Paste only one of this two following codes and adapt the “alias=” value with the previously copied Bookmark Alias :
To display Virtual Authenticator inline at the place you want in your page: in the HTML/PHP code, find the “<head>” HTML tag, and paste this line just before the first “<script>” tag :
CODE<script type="text/javascript" src="https://ult-inwebo.com/va/client.js"></script>Find the “<body onload=“OnLoad()”>” tag and paste this just after the body tag:
CODE<div id="iwVaDetect" data-action="authentication" data-container="myContainer" data-lang="en" data-alias="1a2b3c4d5e6f7g8h9i0j1a2b3c4d5e6f7g8h9i0j" data-width="auto"></div> <div id="myContainer" ></div>CODE$bodyOr to display Virtual Authenticator as a popup (floating in your page): in the HTML/PHP code, find the “<head>” HTML tag, and paste this line just before the first “<script>” tag :
CODE<script type="text/javascript" src="https://ult-inwebo.com/va/client.js"></script> <script language="JavaScript"> VA_jQuery(document).ready(function(){ iwpopup("myContainer", "my_VA_div", function() { iwstart("my_VA_div", function(iw, data) { if (data.action == "authentication" && data.code == "ok") { iw.insertFields(data.result); } if (data.type == "error" && data.code == "nok" && data.result.reason == "no_profile") { console.log('VA KO : no profile'); } }); }); })t </script>Find the “<body onload=“OnLoad()”>” tag and paste this just after the body tag:
CODE<div id="my_VA_div" data-action="authentication" data-container="myContainer" data-lang="en" data-alias="1a2b3c4d5e6f7g8h9i0j1a2b3c4d5e6f7g8h9i0j" data-width="auto"></div> <div id="myContainer" style="margin-left:350px; display:none;"></div>
Save this changes with the “Save button”
Apply Access Policy for the changes to be applied
Type the F5 Login page URL to test it. You now should see Virtual Authenticator token displayed in your login page. If not, please ensure that your current web browser is enrolled as a device in inWebo, this is mandatory for Virtual Authenticator to be loaded in your login page.
OPTIONAL: Helium integration in the F5 login page
IMPORTANT: For all inWebo services created after the 10th of mai 2016, Virtual Authenticator is the default browser token. Helium is not usable. Helium is activated just in the case you created your inWebo service as a “White Label Service”.
Instead of having to generate manually an OTP with your phone to login through the radius, you may want to integrate InWebo Helium to the F5 login page to authenticate your users. To do so, you have to do this 2 step configuration
Create a Secure Site in your MyInWebo Administration Console, and activate Helium on it
Open your MyInwebo Admin Console
In “Secure Sites” Tab > “Secure Sites”, choose “WebService Connector” or “radius push” in the “Add a Secure Site of type…” drop-down list
Give it a Name
Fill the 'Called Url' field with the URL of your BigIp login page
Click “Automatic Detection” to recognize the form name and login/password field names
If they are not recognized, manually “e1” for 'Form name', “username” for 'Login' and “Password” for 'password.
Click “Add” to add this new site, then close.
Edit this newly added service with the pen button :
Copy-paste somewhere the “Helium alias” value for a later use in the next step
That's all for the InWebo part
Next, you need to customize the login page on your F5 device :
Connect to your F5 Administration interface.
Go to MAIN tab > Access Policy > Customization > Advanced
A new window opens, click on the “Edit Mode” button to choose “Advanced”
Under the “Customization Settings”, expand “Access Profiles” with the [+] sign
Expand the profile corresponding to your radius configuration, then expand “Access Policy”, then “Logon Page” twice in order to be able to view/edit “login.inc” file
In the HTML/PHP code, find the “<head>” HTML tag, and paste this line just before the first “<script>” tag :
CODE<script type="text/javascript" src="https://ult-inwebo.com/webapp/js/helium.min.js"></script>find the “<body onload=“OnLoad()”>” tag
Paste this code in a new line just after the body tag and adapt the “alias=” value with the previously copied Helium Alias :
CODE<div id="inweboDetect" alias="1a2b3c4d5e6f7g8h9i0j1a2b3c4d5e6f7g8h9i0j" action="authenticate" lang="auto" style="display:none"></div>Finaly, paste either of the following HTML codes :
to display Helium inline at the place you want in your page :
<div id="helium_form" style="align:center; width:460px; margin-left:60px"></div>
<div id="heliumDesign" top="10" left="40" rounded="1" shaded="1" skin="default" maincolor="#28AA28"
withlogo="1" withactiontitle="1" withborder="1" bordercolor="#28AA28" bgcolor="#999999" withtitle="1"
titlebgcolor="#28AA28" titlecolor="#FFFFFF" displaytype="inline" container="helium_form"></div>to display Helium as a popup (floating in your page):<file>
<div id="heliumDesign" top="10" left="40" rounded="1" shaded="1" skin="default" maincolor="#28AA28"
withlogo="1" withactiontitle="1" withborder="1" bordercolor="#28AA28" bgcolor="#999999" withtitle="1"
titlebgcolor="#28AA28" titlecolor="#FFFFFF"></div>
</file> Save this changes with the “Save button”
Apply Access Policy for the changes to be applied
Type the F5 Login page URL to test it. You now should have the Helium Token that appear in your login page. If not, please ensure that your current web browser is enrolled as a device in InWebo, this is mandatory for Helium to be loaded on the login page.
Configuring InWebo SAML authentication on a F5 Big-Ip APM
1. Configuring a custom SAML IdP connector
As it's easier to create the IdP connector from IdP metadata, you first need to add a SAML connector on the InWebo IdP part.
Connect to the InWebo administration console https://www.myinwebo.com/console
Click on the “Secure Sites” tab
Add a “SAML 2.0” connector by choosing in the drop-down list of the “connectors” section.
Optionnal : give it a name
Leave SP Metadata field blank for the moment
Validate by pressing the “Add” button.
A successfull message updates the windows as well as the new generated IdP Metadata. Click the “Download inWebo IdP SAML 2.0 metadata in XML format” link to download them on your computer.
Now connect to your F5 BIG-IP Administration interface in a new browser window.
We have to configure a SAML IdP connector so that Access Policy Manager (as a SAML service provider) can send authentication requests to this IdP, relying on it to authenticate users and to provide access to resources behind APM.
On the Main tab, click Access Policy > SAML > BIG-IP as SP. The BIG-IP as SP screen opens and displays a list of local SP services.
On the menu bar, click External IdP Connectors. A list of SAML IdP connectors displays. Click Create > From Metadata. The Create New IdP Connector screen opens.
In the Name field, type a unique name for the SAML IdP connector.
In the Select File, browse the file you just downloaded above in the InWebo administration console.
Give a unique Identity Provider Name.
Click OK. The screen closes.
APM creates a SAML IdP connector. It is available to be attached to a SAML SP service.
2. Configuring a SAML SP service
Configure a SAML SP service for Access Policy Manager to provide AAA authentication, requesting authentication and receiving assertions from a SAML IdP.
Go to MAIN tab > Access Policy > SAML > BIGIP as SP and clic the (+) sign to add a new definition. The Create New SAML SP Service screen opens.
Type a unique name for the SAML SP service in the mandatory corresponding field
In the Entity ID field, type a unique identifier for the service provider that includes the URI that points to the virtual server with the BIG-IP system and a unique path. For example, if you type https://bigip-sp/sp, then https:/bigip-sp points to the virtual server you use for APM as a SAML service provider and “/sp” is a unique string that APM uses to distinguish one service provider from another on this BIG-IP system.
Optional: In the Relay State field, type a value. The value can be an absolute path, such as hr/index.html or a URI, such as https://www.abc.com/index.html. It is where the service provider redirects users after they are successfully authenticated and have been allowed by the access policy. When APM receives the relay state from the Identity Provider in addition to assertion, then it uses the value received from the IdP to redirect the user. Otherwise, APM uses the value from this configuration.
From the left pane, select Security Settings. The screen changes to display the applicable settings.
Select Signed Authentication Request if you want this BIG-IP system to send signed authentication requests to the SAML IdP.
Leave Want Encrypted Assertion unchecked.
Select Want Signed Assertion (this is selected by default).
From SP's Authentication Signing/Assertion Decryption Private Key, select a key from the BIG-IP system store on this device. You can select a private key only when you select at least one of these check boxes: Signed Authentication Request and Want Encrypted Assertion. APM uses this private key to sign the authentication request to the IdP and to decrypt an encrypted assertion from the IdP.
From SP Certificate, select a certificate. APM includes this certificate in the SAML SP metadata that you export. After the SAML SP metadata is imported on the IdP, the IdP can use this certificate to verify a signed authentication request and to encrypt an assertion.
Click OK. The screen closes.
APM creates the SAML SP service. It is available to bind to SAML IdP connectors and to export to a metadata file.
3. Binding a SAML SP service to SAML IdP connectors
Select a SAML SP service and bind the InWebo SAML IdP connectors to it so that this device (BIG-IP system as a SAML service provider) can request authentication from the InWebo external IdP through its connector.
On the Main tab, click Access Policy > SAML > BIG-IP as SP. The BIG-IP as SP screen opens and displays a list of local SP services.
Select the SAML SP service you just created from the list.
Click Bind/Unbind IdP Connectors. A pop-up screen displays a list of any IdP connectors that are associated with this SP service.
To add the InWebo SAML IdP connector to the list, click Add New Row.
Complete the configuration: select the InWebo connector from the SAML IdP Connectors list in the new row. When you bind only one IdP connector to an SP service, you do not need to fill in the Matching Source and Matching Value fields.
Click the Update button. The configuration is not saved until you click OK.
Click OK. APM saves the configuration. The screen closes.
The InWebo SAML IdP connector that you selected is now bound the SAML SP service.
4. Exporting SAML SP metadata from APM
You need to convey the SP metadata from APM to the InWebo SAML IdP that provides authentication service to this SP. Exporting the SAML SP metadata to a file provides you with the information that you need to do this.
On the Main tab, click Access Policy > SAML > BIG-IP as SP. The BIG-IP as SP screen opens and displays a list of local SP services.
Select the SP service created above from the list and click Export Metadata. A popup window opens, displaying No on the Sign Metadata list.
If no need to sign those metadata, just click OK. APM downloads an XML file.
You now have to use the information in the download XML file to fill the SP metadata on the InWebo IdP SAML Connector.
open the donwloaded XML metadata in a text editor and copy the entire content of that file in the clipboard of your computer (CTRL+C most of the time under Windows systems).
Back to your InWebo administration console (https://www.myinwebo.com/console), click on the “Secure Sites” tab.
Edit the previously added “SAML 2.0” connector by clicking the pen icon on the right of the connector name in the “connectors” section.
Paste the Metadata from the clipboard (CTRL+V most of the time under Windows systems) in the Metadata Service Provider (SP) section of the opened window.
Validate by clicking the Update button, then close the window with the Cancel button.
5. Configuring an access policy to authenticate with the InWebo SAML IdP connector
Note : We assume that you already have at least one Access Profile configured. If not, please refer to your F5 admin guide in order to configure an access profile before you start this task.
When you use this BIG-IP system as a SAML service provider, configure an access policy to direct users to an external SAML IdP for authentication .
On the Main tab, click Access Policy > Access Profiles. The Access Profiles List screen opens.
In the Access Policy column, click the Edit link for the access profile you want to configure to launch the visual policy editor. The visual policy editor opens the access policy in a separate screen.
Click the (+) sign anywhere in the access policy to add a new action item. An Add Item screen opens, listing Predefined Actions that are grouped by General Purpose, Authentication, and so on.
From the Authentication area, select SAML Auth and click the Add Item button. The SAML Auth properties window opens.
In the SAML Authentication SP area from the AAA Server list, select the SAML SP service you created before and click Save. The Access Policy window displays.
If needed, change the Successful rule branch from Deny to Allow and click the Save button.
At the top of the window, click the Apply Access Policy link to apply and activate your changes to this access policy.
Click the Close button to close the visual policy editor.
Your access policy should at least look like this one :
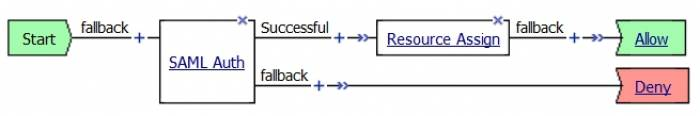
You now have an access policy that should work correctly and uses SAML authentication through InWebo as IdP.
